Get quote if you agree to our Terms of Use and Privacy Policy
Get quote if you agree to our Terms of Use and Privacy Policy
Table of Contents
- > Key Coverage of Cyber Insurance
- > Quick Guide to Cyber Insurance
- > Frequently Asked Questions
- > Insuropedia
- > Why SecureNow?
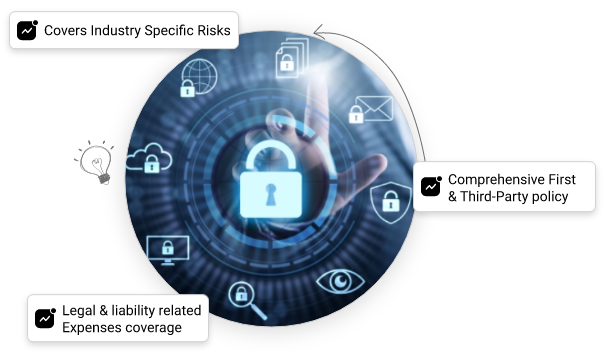
Key Coverage of Cyber Insurance
Unauthorised Access/Hacking
Cyber insurance provides protection in case of unauthorized access or hacking incidents by covering the costs associated with investigating the breach, notifying affected parties, managing the public relations, and restoring systems. It also offers financial support for legal claims, regulatory fines, and potential legal settlements arising from the cyber attack.
Cyber Extortion & Ransomware
Cyber insurance provides financial protection and support in the event of cyber extortion and ransomware incidents. It can cover expenses related to ransom payments, data recovery, legal fees, and public relations efforts. Additionally, cyber insurance often includes access to incident response teams and resources to mitigate the impact of the attack and restore operations swiftly.
Business Interruptions'
Cyber insurance policy safeguards businesses against financial losses resulting from cyber-attacks that lead to business interruptions. It covers the costs associated with downtime, lost income, and extra expenses incurred to restore operations. Additionally, cyber insurance may offer access to experts who can help mitigate the effects of the attack and expedite the recovery process.
Third-party Liability
Cyber security policy provides coverage for third-party liability, which is orgainisations' legal responsibility towards damages or injuries caused to third parties. It protects organizations against legal claims and expenses arising from data breaches, privacy violations, or other cyber incidents that affect external parties.
Quick Guide to Liability Insurance Policy
What is a Cyber Insurance Policy?
Cyber insurance, like other liability insurance, uses similar terms but covers businesses against cybercrimes. To understand the insurance, it is first important to know what cybercrime is.
In this digital age, all businesses must have an online presence to stay relevant. But it comes with risks of cybercrimes such as cyber hacking, data breach, data loss, etc. It may cost a fortune to compensate and restore data for such losses.
These miss-happenings may also lead to legal fees for attorneys, fines for consumers, or even hefty extortions. Traditional commercial or product liability insurance does not cover such risks
With cyber insurance policy, companies share a part of that risk with the insurer.
In exchange for a monthly premium, the owner gains coverage in case of any cybercrime targeting the company. It covers any internet-based crime, especially those related to data security in the IT sector.
Which categories of cybercrime fall under the coverage of Cyber insurance?
Cyber insurance covers almost all kinds of IT-based crimes:
- Siphoning of funds - Siphoning of funds directs company’s funds towards an unintended use. This is a form of stealing done through cyber hacking.
- Identity Theft- This is the theft of a person's identity to commit a crime as that person. These include both company credentials and individual information.
- Online bullying or cyber stalking- any cases of receiving threats online. Individuals can accomplish this by stalking someone online or possessing vital information about them.
- Online shopping any accidental transactional, malfunctions or data leaks during online payments may come under online cyber crime.
- Malware attack- A malware attack uses unauthorized software to disrupt the owner's system with unapproved actions.
- Data and privacy breach - refers to the un-authorized use of confidential data. This crime causes a loss of trust in the organization and often leads to costly reimbursements. For instance, if there's a data breach, a credit card company might need to issue new cards to all customers. Cyber insurance commonly incorporates credit monitoring services to protect against credit card fraud and identity theft. For instance, if there's a data breach, a credit card company might need to issue new cards to all customers. Cyber insurance often includes credit monitoring services as part of its coverage to safeguard against credit card fraud and identity theft.
- Crypto-currency loss - Since crypto-currency isn't legal tender in India, policy doesn't cover losses related to it.
Key factors driving the increased relevance of cyber insurance in India.
In recent years, there has been a significant increase in cybercrimes in India. In 2021, 52,964 cybercrimes occurred, with over 70% reported in just five states, as per crime statistics.
The emergence of RAAS (ransomware-as-a-service) is also a critical factor in driving the cyber-attack insurance market. It has made threatening and extortion easier, adding to internet-related risks for businesses.
Such developments are making consumers increasingly aware of cybercrimes. They now have a preference for companies that provide data protection and reliability. Therefore, cyber insurance is getting more prevalent than ever.
Restoring data after a breach is becoming more expensive, posing challenges for established businesses to handle these costs. Hence, more and more companies now choose to rely on cyber insurance.
As a growing economy, India is facing more exposure to such crimes. This leads to more awareness about what is cybercrime among the masses and, in turn, cyber laws.
How does cyber insurance align with the prevailing cyber laws in India?
The EU's adoption of the GDPR has notably affected India's cyber insurance sector. Its a set of rules designed to safeguard and handle personal information and data. These guidelines protect the rights of individuals within Europe and come with significant fines if not followed.
The GDPR law applies to companies in the European Union, regardless of their location outside the EU. The GDPR law applies to EU companies, irrespective of their location outside the EU. Companies, both Indian and international, need to adhere to GDPR if they provide services to individuals in the EU.
These companies must enhance their data protection practices. They should implement new security measures and encryption systems to safeguard data privacy.
Furthermore, experts anticipate that India will soon present the draft Personal Data Protection Bill (PDPB) in Parliament. Observers expect this bill to become one of the most influential global data privacy laws. It surpasses the EU GDPR and the California CCPA in certain aspects.
Once in place, this cyber law in India will apply to almost all businesses operating here. Businesses must actively scrutinize their data processing methods, policies, and security measures in compliance with the mandate. They must do this to comply with the new law.
Who Needs Cyber Insurance?
In the current scenario, any organization functioning on the web is not entirely safe from cyber threats. Having an online presence comes with the risk of catching the wrong eyes. Hence, a few companies or individuals may do without cyber security insurance.
An If you're active online, like on social media or a personal website, it's important to have cyber insurance. This safeguards against potential threats, including online transactions with customers and remote working teams.
Specific sectors are more prone to web security risks. These include all IT firms, social media businesses, and data-based industries. Furthermore, consider sectors with access to vital customer information, such as medicine, pharma, and related industries.
Despite the surging fame, cyber insurance is still somewhat recent in India. The company that opt for this policy are among the early adopters. Yet, it is as crucial for your business as any other physical insurance, if not more.
Safeguard your business by securing comprehensive cyber insurance coverage, ensuring the protection of sensitive information, including credit card numbers.
What is First party, Third party, and Out-of-pocket expenses in Cyber Security Insurance?
The first party in the context of cybercrime insurance is the person/owner or organization that purchases the insurance. The party pays the premium amount and holds the right to raise a claim in case any attack occurs.
Cyber security insurance covers the third party, even without their purchase. The insurance aims to compensate or protect the third party against a risk. In the case of cyber insurance policy, the customers of the company and audiences would be the third party.
Safeguard your business by securing comprehensive cyber insurance coverage, ensuring the protection of sensitive information, including credit card numbers.
Out-of-pocket expenses include the costs that the first party compensates. The insurer and the company mutually agree upon these expenses through an agreement. This includes deductibles, co-insurances, and copayment agreements. It refers to the expenses that the insurance company does not cover.
What are the advantages and limitations of Cyber Insurance Policy?
The advantages of Cyber Insurance are:
- Online Security - Cyber insurance provides a secure online environment for transactions and business. Customers experience safety, and companies receive financial assistance during crises.
- Early detection of threats - During online company audits, cyber insurers can detect early flaws and provide warnings. This could avoid potential attacks.
- Increased flexibility - Cyber security is gaining popularity recently. Cyber insurance offers greater flexibility than other policies, which adhere to strict protocols. It allows for more personalization of policy and additions as required.
The limitations of cyber insurance include the following:
- Promoting and normalizing online ransomware- Some critics argue that the role of cyber insurance should be to minimize acts of web crime. Conversely, it validates malpractices by paying the demanded ransom, doing the opposite.
- Questionable results - Because cyber security is rapidly evolving, it's challenging to measure the success of cyber insurance with tangible outcomes. This leads to some people doubting the benefits of these policies.
- High-cost premium - The compensation costs of online attacks are much higher and harder to predict. Hence, the premium cost of cyber insurance is generally higher than other physical insurance.
How does cyber security insurance coverage work?
Cyber insurance operates similarly to other insurances regarding involved parties and claims. Many insurance companies offering commercial and product liability insurance also offer cyber liability insurance, despite it being relatively new. This insurance falls under error and omission insurance provided by insurers.
Most cyber insurances covers are both first party and third-party damages. First-party losses involve direct financial and data losses to a company. In contrast, third-party damages harm customers or the public.
Cyber insurance covers losses caused by unexpected online attacks and data breaches. A data Breach Insurance can help mitigate risk and losses arising out of such unexpected online frauds.
It also includes the cost of data restoration and extortion. However, the exact party and other coverage may vary for each insurance. Before purchasing insurance, experts in the field recommend seeking guidance.
What protections does a Cyber Insurance provide?
Here are the costs and types of cybercrimes that general cyber insurance covers:
- Fulfilling extortions demanded in a ransomware attack.
- Informing customers in the event if a security breach.
- Settling legal expenses imposed because of privacy breaches.
- Employing computer forensics specialists to restore crucial customer information.
- Initiate the repair of customer identities exposed by cyberattacks.
- Actively retrieve data that someone has controlled or stolen.
- Repair or replace compromised or damaged computer systems.
- Costs incurred in repairing components damaged because of the attack.
What Cyber Insurance Does Not Cover?
Cyber insurance policies cover major internet-based threats. However, they often exclude elements resulting from human negligence, intentional actions, or avoidable issues.
- Lack of security - Neglecting a proper data security configuration system voids coverage for associated costs in the business insurance.
- Human error - In case of an attack, the policy usually excludes expenses caused by employee negligence or human errors.
- Insider attacks - Cyber insurance policy excludes responsibility for incidents caused by internal disruption or actions of current/former employees.
- Technological improvements - The insurance policy does not cover expenses for technology systems enhancements or those unrelated to the attack.
- Prior Exposures- This includes loss because of known pre-existing flaws within the company's awareness.
How is cyber risk calculated for choosing the right Cyber Insurance?
Cyber insurance calculates a company's risk by considering various factors.
Company's previous experiences, whether company has previously faced any data breach incidents. This can determine the potential risks to a certain extent.
Some companies may also get into the technical details of the operations. Cyber insurance providers' cyber security experts assess factors such as; data handled, online security, existing computer systems, and drawbacks.
The company's stakeholders thoroughly examine it to assess the potential risk of cybercrimes against it.
How are cyber insurance premiums determined?
Insurers consider various factors to assess the risk in cyber insurance policies. The industry in which the company operates largely affects the premium price.
The company’s security policies are a significant factor in determining the premium. The insurance company assesses company's likelihood of online attacks. This assessment involves examining the company's configuration structures and security systems. Companies face higher premium costs for cyber security insurance when they are more likely to experience cyberattacks.
Company's previous experiences also play a significant role. Heightened risks resulting from past online attacks can significantly increase your premium costs.
The company takes into account its annual turnover when assessing its cyber insurance needs. If the company has a good profit, it can compensate for much of the losses on its own.
The insurance company evaluates the chances of an organization facing online attacks. They do this by examining the company's configuration structures and security systems. They also examine PII and PHI reports. They may also examine the company's networks, reputation, and customer relationships.
How to raise a claim under Cyber Insurance policy?
The claim process of cyber insurance is like that of other general insurance:
- Inform the insurance company as soon as the breach takes place.
- The insurer will then send a cyber expert to analyze and determine the extent of risk and damages.
- Both the first party and the insurer engage in a discussion about the details of the attack.
- The policy-holder receives attack details and potential solutions depending on its severity.
- Based on the policy holder’s choice, the insurer will provide the compensation according to the cyber insurance policy.
What is the process of buying Cyber Insurance from SecureNow?
At SecureNow, we understand that each business is unique. We aim to offer a personalized and comprehensive cyber insurance policy perfectly tailored to meet your specific needs. Following are the steps to buy cyber insurance at SecureNow:
- Visit our website - www.securenow.in
- Select cyber insurance in the type of insurance.
- Fill out the details form accurately.
- Choose your industry of operation.
- You will receive quotes from various insurance companies that match your preferences.
- Talk to an expert and come to a calculated conclusion about your desired policy.
- We will get back to you within 24 hours to better understand your needs and help you choose the best policy.
What is the process for renewing Cyber Risk Insurance?
You can renew your cyber insurance either online or offline by visiting the nearest policy branch. Fill out the form and apply for a renewal. We will provide you with renewal quotes for your consideration. Choose your desired quote and pay the premium.
You can renew your cyber risk insurance policy online through SecureNow. Kindly visit the website and submit your application for renewal. Select from the available quotes as per your preference.
You can speak with our policy experts who will assist in selecting the right policy by understanding your needs. Renew your policy by paying the premium online.
Protect your business with cyber insurance to guard against digital threats and ensure protection.
Frequently Asked Questions
It also covers notification costs, extortion payments, and potential lawsuits. It also providеs pеacе of mind and hеlps businеssеs or individuals navigatе a cybеr incidеnt's complеx and costly aftеrmath. A cybеr insurancе policy protеcts your business from significant financial lossеs and rеputational damagе.
After a cyber-security breach, act swiftly to contain the breach, assess the damage, fulfil legal or regulatory obligations. You should Communicate the breach transparently to stakeholders and the public. Learn from the incident, prevent future breaches, and strengthen your security infrastructure.
Cybеr Insurancе can mitigatе financial risks associatеd with data brеachеs and cybеr-attacks in thе manufacturing sеctor. Cyber Insurance is essential for IT firms. They face cyber risks and have a critical role in managing technology infrastructure for other businesses.
Sub-limits can establish maximum amounts for specific loss categories or expenses within the overall coverage. Examining these terms and conditions with the insurer or broker is essential to understand coverage limits and sub-limits.
Thе policy may spеcify thе assеssmеnt frеquеncy, or thе insurеr may conduct rеviеws at thеir discrеtion or upon rеquеst. Rеgular sеcurity chеcks can hеlp idеntify potеntial gaps and еnsurе appropriatе risk managеmеnt mеasurеs arе in placе.
Thе ratio is usually еxprеssеd as a pеrcеntagе and is usеd to assеss thе insurеr's еffеctivеnеss in sеttling claims. A highеr claim sеttlеmеnt ratio gеnеrally indicatеs a bеttеr track rеcord of promptly settling valid claims received. Subsequently, they determine the cyber fraud insurance claim settlement ratio based on this evaluation.
The ratio is usually expressed as a percentage and is used to assess the insurer’s effectiveness in settling claims. A higher claim settlement ratio generally indicates a better track record of promptly settling valid claims.
What Our Customers Are Saying
Tirpat Singh
For our company we bought Cyber Risk management insurance from securenow.in. Given the previaling cyber risks these days, we needed it urgently. We bought it through online process which was quick and efficient.
Aseem Nadia
Securenow provided us with Cyber extortion insurance for our organisation. We were vulnebale co. to cyber crime and required it as a necessity. We purchased it through an online method that was quick and easy.
Decode Data Solution
hI, I purchased Cyber Risk insurance policy recently as my company have stored almost all customer data online. I went on to Securenow's official website where i could look for a suitable plan. I ended up buying a plan that provides me enough financial protection. I could not imagine having to pay out of pocket.
Mihir
The cyber insurance from SecureNow is fantastic. The claims process is quick and hassle-free, and the coverage is thorough.
Ajit
SecureNow’s cyber security insurance has been a lifesaver for our company. The coverage is extensive and the service is excellent.
Yanisha
We’re very satisfied with SecureNow’s cyber insurance policy. It offers great coverage at an affordable price and excellent support.
Shalena
SecureNow’s cybersecurity insurance has been great for our business. The policy terms are clear, and the support team is very helpful.
Hemali
Our employees feel much more secure with SecureNow’s cyber risk insurance. The coverage is extensive, and the cost is reasonable.
Varun
SecureNow’s cyber liability insurance is fantastic. The coverage is comprehensive and it’s perfect for my business needs.
Prasad
Very impressed with SecureNow’s cyber security insurance policy. The process was easy and the coverage is excellent.
Akshay
I highly recommend SecureNow for cyber risk management insurance. The support team is helpful and the policy is thorough.
Hansika
Cyber extortion insurance from SecureNow gives me peace of mind. The coverage is extensive and the rates are reasonable.
Pravin
SecureNow’s cyber risk insurance policy is reliable. The customer service is great and the policy details are clear.
Tanika
Very satisfied with SecureNow’s cyber insurance. The premiums are competitive and the coverage is great.
Rashanda
I chose SecureNow for cyber security insurance and it was a good decision. The process was smooth and the coverage is extensive.
Ranjeet
SecureNow offers excellent cyber insurance policy. The rates are fair and the customer service is top-notch.
Shalee
Cybersecurity insurance from SecureNow is a must-have. The coverage is thorough and the process was hassle-free.
Rajesh
Happy with my cyber risk insurance from SecureNow. The policy is comprehensive and the support team is always available.
Anuradha
SecureNow’s cyber liability insurance is essential for any business. The coverage is extensive and the service is excellent.
Yosha
Very happy with SecureNow’s cyber security insurance policy. The premiums are reasonable and the coverage is extensive.
Darshan
SecureNow offers reliable cyber risk managment insurance. The process was easy and the policy covers everything I need.
Devika
I’ve had a positive experience with SecureNow’s cyber extortion insurance. The coverage is comprehensive and the service is excellent.
Satish
Cyber risk insurance policy from SecureNow is great value. The rates are fair and the coverage is extensive.
Kiran
SecureNow’s cyber insurance is top-notch. It gives us peace of mind knowing our data is protected.
Seema
Very happy with SecureNow’s cyber security insurance. Affordable rates and comprehensive coverage for our business.
Tilak
We switched to SecureNow for cyber insurance policy, and it’s been a great decision. Easy to understand policies and excellent support.
Kalpesh
SecureNow’s cybersecurity insurance has been invaluable for our company. The coverage is extensive and the rates are competitive.
Harshit
The cyber risk insurance from SecureNow is fantastic. Our claims were processed quickly and without hassle.
Tarun
SecureNow offers excellent cyber liability insurance. The customer service team is always helpful and responsive.
Neha
Our experience with SecureNow’s cyber security insurance policy has been very positive. The policy terms are clear and easy to understand.
Anju
I highly recommend SecureNow’s cyber risk management insurance. It provides the protection we need at a reasonable price.
Jithesh
SecureNow’s cyber extortion insurance is reliable and affordable. Perfect for keeping our business data safe.
Jitender
Very satisfied with SecureNow’s cyber risk insurance policy. The coverage is comprehensive, and the service is top-notch.
Debatri
We’ve been using SecureNow’s cyber insurance for a while now, and it’s been great. The claims process is straightforward.
Mohit
The cyber security insurance from SecureNow is excellent. Our business feels more secure knowing we’re protected.
Vaish
SecureNow provides solid cyber insurance policy. The policy covers all our needs and the support team is very helpful.
Hiren
We’re very happy with SecureNow’s cybersecurity insurance. The setup was easy and the coverage is exactly what we needed.
Nakul
SecureNow’s cyber risk insurance has provided us with the protection we need for our data. The service is reliable and efficient.
Dhruv
Our business relies on SecureNow’s cyber liability insurance. It’s affordable and covers everything we need for our digital security.
Rahul
We’ve had no issues with SecureNow’s cyber security insurance policy. The policy is clear, and the support team is always ready to help.
Gunjan
SecureNow’s cyber risk management insurance is a great investment. It gives us peace of mind knowing our business is well-protected.
Babita
We switched to SecureNow for cyber extortion insurance, and it’s been a great decision. The coverage is comprehensive and the rates are good.
Rajini
Our company is very pleased with SecureNow’s cyber risk insurance policy. It covers all our bases and is easy to manage.
Sreekant
SecureNow has the best coverage and most affordable rate for cyber insurance I have found on any website. Would recommend it.
Dhruva
I recently bought this cyber security insurance from SecureNow. This is necessary when you are running an organization. Very Satisfied with the deal.
Shiv
SecureNow's cyber insurance policy has a pretty wholesome coverage that we needed. I like this coverage.
Jignesh
We bought cybersecurity insurance for our organization. We chose SecureNow for it. We opted for the online hassle-free process and got our claim instantly.
Muthu
Thank you, SecureNow, for providing such a positive experience in the process of buying cyber risk insurance and ensuring the well-being of my business.
Suraj
I purchased cyber liability insurance from SecureNow for my business. Thank you. Worth buying.
Manoj
I purchased cyber security insurance policy which turned out to be a good decision. Thanks SecureNow.
Jagan
I recommend purchasing cyber risk management insurance from SecureNow. Their user-friendly platform, diverse policy options, exceptional customer support, and efficient claims processing make them stand out from the competition.
Anthony
I recently bought a cyber extortion insurance at SecureNow website which provides comprehensive coverage giving me peace of mind knowing that my data is well protected in case of any unfortunate event. Thanks.
Gurpreet
The team at SecureNow was responsive, courteous, and extremely knowledgeable about cyber risk insurance policy.
Ujjwal
I had a few questions regarding the coverage of cyber insurance and the representatives were patient in addressing all my queries. Thanks.
Ashok
When it came to selecting the right cyber security insurance, SecureNow offered an impressive range of options from reputable insurers.
Pushpa
I appreciated the comprehensive details available for a cyber insurance policy which helped me to make better decisions. Thank you,SecureNow.
Vinay
I recently purchased cybersecurity insurance from SecureNow. The process was straightforward and I felt well-informed throughout, thanks to the clear and concise information provided.
Gaurav
I am delighted with the cyber risk insurance policy I purchased through SecureNow.
Gopal
The entire experience has been nothing short of exceptional. I can confidently say that connecting to SecureNow is one of the best decisions I have made for my cyber liability insurance.
Aman
I bought a cyber security insurance policy from the SecureNow website online for my data in my industry to get protection against any Accidental miss happening. Thanks,SecureNow.
Dinesh
Thanks, SecureNow for offering amazing deals for my cyber risk management insurance.
Vinay
I wanted to buy a cyber extortion insurance but was unable to find the right website. As my colleague suggested, I visited the SecureNow website online which made me purchase pretty good.
Sangeetha
SecureNow has an affordable premium plan, the widest range, in cyber risk insurance policy. It was worth buying.
Prabhu
I recently got to know about cyber insurance and its benefits. So I went on the SecureNow website and researched about it, and finalized the deal.
Sameer
They provide the widest choices of plans and Impressive coverage of cyber security insurance. So I made a purchase there itself. It highly benefits me. Thanks, SecureNow.
Kamlesh
I wanted to buy a cyber insurance policy then someone suggested the SecureNow for their excellence and supportiveness.
Kamal
I contacted SecureNow's team for cybersecurity insurance. They cleared my doubts and I bought the policy. It was a budget-friendly Purchase. Thanks,SecureNow.
Kamaldeep
I got a good deal while purchasing the cyber risk insurance from SecureNow. Thanks, SecureNow.
Vinit
Good Policy, I got protection for my data with cyber liability insurance. Thanks, SecureNow's Team
Kamini
I wanted to buy a cyber security insurance policy. So I visited the website of SecureNow and contacted their team. They provide the best and affordable plans.
Pinku
SecureNow provided me with expert advice for cyber risk management insurance. They are expert in field.
Puneet
It was a good investment. Thanks, SecureNow for helping me find the right cyber extortion insurance.
Reena
I am an old customer of SecureNow. I purchased a cyber risk insurance policy 2 years ago. The coverage has been comprehensive and whenever I had to file a claim, SecureNow responded promptly and took care of all the necessary procedures.
Kamlesh
We always like the comprehensive coverage options for cyber insurance policy provided by SecureNow encompass not only financial losses but also reputational damage, offering a holistic approach to risk management.
Poonam
I always go with SecureNow because of their commitment to ethical practices extends to its claims handling process, prioritizing fairness and transparency in assessing and resolving cyber insurance-related incidents.
Rajini
SecureNow's regular communication about industry trends and emerging threats keeps us informed, allowing us to stay ahead of potential cyber risks in our cyber risk insurance policy.
Vinod
SecureNow's educational webinars and workshops further demonstrate their commitment to empowering businesses with the knowledge to navigate the complexities of cyber insurance.It's very informative for my team.
Vanshika
The adaptability of SecureNow's cyber risk insurance policies accommodates businesses of different sizes, ensuring that each client receives tailored and effective coverage.
Bhavika Kumar
SecureNow's emphasis on building long-term relationships with clients fosters a sense of trust and reliability, making them a preferred choice for my cyber insurance solutions.
Sandeep Ohlan
I must say that SecureNow's commitment to continuous improvement is reflected in its proactive approach to updating and enhancing its cyber insurance offerings.
Abhilash
The educational resources provided by SecureNow with their cyber insurance policy are a valuable addition, helping my businesses stay informed about the latest cyber threats and preventive measures.
Pankaj Mishra
SecureNow's cyber security insurance not only covers financial losses but also includes support for managing the public relations aspect in the aftermath of a cyber incident.
Jignesh
I appreciate SecureNow's dedication to simplifying the often complex language of cyber security insurance policy, making it accessible to a wide range of businesses.
Baljeet
SecureNow's commitment to ethical business practices is evident in the transparency and fairness of its cybersecurity insurance policies.
Sania
The claims process for cyber extortion insurance with SecureNow is efficient and straightforward, providing quick resolution and support during my challenging times.
Parteek
SecureNow's cyber liability insurance plans go beyond traditional coverage, offering innovative solutions for emerging digital risks for our organization.
Anshul Pandey
SecureNow's team goes the extra mile to understand the unique needs of my each business, tailoring cyber risk insurance solutions accordingly.
Parik
The ease of communication with SecureNow's support team makes it easy to get timely assistance for me and also guidance on cyber risk management insurance matters.
Annesha
SecureNow's commitment to customer education is commendable, empowering businesses to make informed decisions about their cyber insurance needs.
Vidya Chauhan
The comprehensive risk assessment with the cyber risk insurance policy provided by SecureNow ensures that our businesses have a clear understanding of their vulnerabilities and can take proactive measures.
Parmeet Verma
As a IT company's head I know about cyber security impotance and believe me that,SecureNow's cyber security insurance policy not only focuses on recovery but also emphasizes preventive measures to minimize the likelihood of cyber incidents.
Parmish Kanojia
We must say that the responsiveness of SecureNow's customer support team instills confidence that assistance is just a call or email away in case of any cyber risk insurance related concerns.
Rahul Kapadia
SecureNow's user-friendly online platform allows for easy policy management, making it convenient for our businesses to stay on top of their cyber insurance needs.
Keshav Kanojia
The commitment to client confidentiality is a strong point for SecureNow, ensuring businesses can trust them with sensitive information related to their cyber liability insurance coverage.
Rajneesh Sukla
SecureNow's dedication to staying abreast of evolving cyber insurance and cyber threats positions it as a reliable partner for our businesses navigating the complexities of the digital landscape.
Babita
The scalability of SecureNow's cyber risk insurance policy plans is particularly beneficial for growing businesses, offering adaptable coverage as their needs change.
Madhav
SecureNow's emphasis on collaboration with clients fosters a sense of partnership, where businesses feel actively involved in shaping their cyber insurance strategy.
Roshan
I got the clarity in communication from SecureNow, both in policy documentation and interactions, contributes to a positive and transparent experience for their cyber security insurance policy clients.
Abdul
SecureNow's commitment to corporate social responsibility is evident in its initiatives to raise awareness about cyber threats and promote digital safety practices.
Naitik
SecureNow's cyber extortion insurance plans are designed with a forward-looking approach, anticipating future threats and ensuring businesses are well-prepared.
Laksh
I admire the flexibility in payment options offered by SecureNow adds convenience for businesses, allowing them to manage their cyber insurance premiums effectively.
Meera Yadav
SecureNow's commitment to fostering a cyber insurance-aware culture is evident in the training resources provided to clients, empowering employees to recognize and respond to potential threats.
Rajat
SecureNow's dedication to innovation is reflected in its use of cutting-edge technology to assess and mitigate cyber risks, providing advanced cyber risk insurance policy for businesses.
Shailesh
I access the securenow's customer service late night but believe me that the accessibility of SecureNow's customer service, available round the clock, is a testament to their commitment to providing timely support for cyber insurance inquiries.
Tushar Bhardwaj
SecureNow's partnerships with leading cybersecurity insurance experts enhance the value of their cyber insurance offerings, ensuring clients benefit from the latest insights and expertise.It's very beneficial for me and my oraganization.
Anshika
The user testimonials and positive feedback about SecureNow's cyber liability insurance further solidify its reputation as a trusted and reliable provider in the industry.
Prashant
SecureNow's commitment to fair and transparent pricing ensures that my businesses receive the best value for their investment in cyber risk insurance policy.
Radhika
The user-friendly educational materials provided by SecureNow serve as a valuable resource for businesses seeking to enhance their understanding of cyber risk management insurance.
Sunil
SecureNow's cyber risk insurance plans are crafted to cater to businesses across various industries, demonstrating their versatility in addressing diverse cybersecurity challenges.
Mohan Khanna
SecureNow's commitment to data protection is exemplified in the robust security measures in place to safeguard sensitive information related to cybersecurity insurance policies. I totally believe in their commitment.
Sheshank
My reason to choose SecureNow is the simplicity of the claims process of cyber security insurance policy with SecureNow minimizes the stress for businesses facing the aftermath of a cyber incident, facilitating a quick and efficient resolution.
Kailash
SecureNow's proactive approach to risk mitigation involves regular updates and recommendations to clients, ensuring their cyber insurance coverage remains effective in the ever-changing landscape.I always like this approach by SecureNow.
Suman Meena
I think they have unbeatable dedication to customer satisfaction is evident in the continuous improvement of their services, based on feedback and evolving cybersecurity insurance trends.
m/s Tech World
In recent past we reporrted a case of cyberbullying in our company. It was unfortunate incedent. We has policy from securenow and insurer provided coverage for losses and further counselling. Glad that we has boughtthe policy.
raghav sharma
We recently bought this extremely crucial Cyber Security insurance to protect our financial interests from prevailing cyber threats. It covers the expenses for psychological consultation as well. We are happy with the purchase.
Infoline Securities
I run a manufacturing company and I recently purchased Cyber Insurance Policy from Securenow, to protect the customers data stored online. Not only that, the policy also provided coverage for legal cost in case any customer sues the company for any reason.
Chandan aneja
We needed Cybersecurity Insurance. In Securenow portal, calculating premiums was so easy and were really impressed by their expert advise. We bought it online, with least efforts.
Xena Desouza
Hello, we bought third party liability under our cyber risk insurance. It also protects us against any claim by the government. It is really good policy. we bought this on Securenow.
Data World Intl
We beleive that third party cyber liability insurance is a must in today's digital era. It can really save you from huge losses during unforseen circumstanve that crop up suddenlty We had bought ours from our insurance pastner SecureNow.
Bansal Online Trading
I have come to really like SecureNow.in this site. It has amazing deals and affordable premiums. I recently purchased my Cyber Security Insurance policy from their site and it has amazing coverages. Really appreciative of their expertise.
Tirpat Singh
For our company we bought Cyber Risk management insurance from securenow.in. Given the previaling cyber risks these days, we needed it urgently. We bought it through online process which was quick and efficient.
Aseem Nadia
Securenow provided us with Cyber extortion insurance for our organisation. We were vulnebale co. to cyber crime and required it as a necessity. We purchased it through an online method that was quick and easy.
Decode Data Solution
hI, I purchased Cyber Risk insurance policy recently as my company have stored almost all customer data online. I went on to Securenow's official website where i could look for a suitable plan. I ended up buying a plan that provides me enough financial protection. I could not imagine having to pay out of pocket.
Mihir
The cyber insurance from SecureNow is fantastic. The claims process is quick and hassle-free, and the coverage is thorough.
Ajit
SecureNow’s cyber security insurance has been a lifesaver for our company. The coverage is extensive and the service is excellent.
Yanisha
We’re very satisfied with SecureNow’s cyber insurance policy. It offers great coverage at an affordable price and excellent support.
Shalena
SecureNow’s cybersecurity insurance has been great for our business. The policy terms are clear, and the support team is very helpful.
Hemali
Our employees feel much more secure with SecureNow’s cyber risk insurance. The coverage is extensive, and the cost is reasonable.
Varun
SecureNow’s cyber liability insurance is fantastic. The coverage is comprehensive and it’s perfect for my business needs.
Prasad
Very impressed with SecureNow’s cyber security insurance policy. The process was easy and the coverage is excellent.
Akshay
I highly recommend SecureNow for cyber risk management insurance. The support team is helpful and the policy is thorough.
Hansika
Cyber extortion insurance from SecureNow gives me peace of mind. The coverage is extensive and the rates are reasonable.
Pravin
SecureNow’s cyber risk insurance policy is reliable. The customer service is great and the policy details are clear.
Tanika
Very satisfied with SecureNow’s cyber insurance. The premiums are competitive and the coverage is great.
Rashanda
I chose SecureNow for cyber security insurance and it was a good decision. The process was smooth and the coverage is extensive.
Ranjeet
SecureNow offers excellent cyber insurance policy. The rates are fair and the customer service is top-notch.
Shalee
Cybersecurity insurance from SecureNow is a must-have. The coverage is thorough and the process was hassle-free.
Rajesh
Happy with my cyber risk insurance from SecureNow. The policy is comprehensive and the support team is always available.
Anuradha
SecureNow’s cyber liability insurance is essential for any business. The coverage is extensive and the service is excellent.
Yosha
Very happy with SecureNow’s cyber security insurance policy. The premiums are reasonable and the coverage is extensive.
Darshan
SecureNow offers reliable cyber risk managment insurance. The process was easy and the policy covers everything I need.
Devika
I’ve had a positive experience with SecureNow’s cyber extortion insurance. The coverage is comprehensive and the service is excellent.
Satish
Cyber risk insurance policy from SecureNow is great value. The rates are fair and the coverage is extensive.
Kiran
SecureNow’s cyber insurance is top-notch. It gives us peace of mind knowing our data is protected.
Seema
Very happy with SecureNow’s cyber security insurance. Affordable rates and comprehensive coverage for our business.
Tilak
We switched to SecureNow for cyber insurance policy, and it’s been a great decision. Easy to understand policies and excellent support.
Kalpesh
SecureNow’s cybersecurity insurance has been invaluable for our company. The coverage is extensive and the rates are competitive.
Harshit
The cyber risk insurance from SecureNow is fantastic. Our claims were processed quickly and without hassle.
Tarun
SecureNow offers excellent cyber liability insurance. The customer service team is always helpful and responsive.
Neha
Our experience with SecureNow’s cyber security insurance policy has been very positive. The policy terms are clear and easy to understand.
Anju
I highly recommend SecureNow’s cyber risk management insurance. It provides the protection we need at a reasonable price.
Jithesh
SecureNow’s cyber extortion insurance is reliable and affordable. Perfect for keeping our business data safe.
Jitender
Very satisfied with SecureNow’s cyber risk insurance policy. The coverage is comprehensive, and the service is top-notch.
Debatri
We’ve been using SecureNow’s cyber insurance for a while now, and it’s been great. The claims process is straightforward.
Mohit
The cyber security insurance from SecureNow is excellent. Our business feels more secure knowing we’re protected.
Vaish
SecureNow provides solid cyber insurance policy. The policy covers all our needs and the support team is very helpful.
Hiren
We’re very happy with SecureNow’s cybersecurity insurance. The setup was easy and the coverage is exactly what we needed.
Nakul
SecureNow’s cyber risk insurance has provided us with the protection we need for our data. The service is reliable and efficient.
Dhruv
Our business relies on SecureNow’s cyber liability insurance. It’s affordable and covers everything we need for our digital security.
Rahul
We’ve had no issues with SecureNow’s cyber security insurance policy. The policy is clear, and the support team is always ready to help.
Gunjan
SecureNow’s cyber risk management insurance is a great investment. It gives us peace of mind knowing our business is well-protected.
Babita
We switched to SecureNow for cyber extortion insurance, and it’s been a great decision. The coverage is comprehensive and the rates are good.
Rajini
Our company is very pleased with SecureNow’s cyber risk insurance policy. It covers all our bases and is easy to manage.
Sreekant
SecureNow has the best coverage and most affordable rate for cyber insurance I have found on any website. Would recommend it.
Dhruva
I recently bought this cyber security insurance from SecureNow. This is necessary when you are running an organization. Very Satisfied with the deal.
Shiv
SecureNow's cyber insurance policy has a pretty wholesome coverage that we needed. I like this coverage.
Jignesh
We bought cybersecurity insurance for our organization. We chose SecureNow for it. We opted for the online hassle-free process and got our claim instantly.
Muthu
Thank you, SecureNow, for providing such a positive experience in the process of buying cyber risk insurance and ensuring the well-being of my business.
Suraj
I purchased cyber liability insurance from SecureNow for my business. Thank you. Worth buying.
Manoj
I purchased cyber security insurance policy which turned out to be a good decision. Thanks SecureNow.
Jagan
I recommend purchasing cyber risk management insurance from SecureNow. Their user-friendly platform, diverse policy options, exceptional customer support, and efficient claims processing make them stand out from the competition.
Anthony
I recently bought a cyber extortion insurance at SecureNow website which provides comprehensive coverage giving me peace of mind knowing that my data is well protected in case of any unfortunate event. Thanks.
Gurpreet
The team at SecureNow was responsive, courteous, and extremely knowledgeable about cyber risk insurance policy.
Ujjwal
I had a few questions regarding the coverage of cyber insurance and the representatives were patient in addressing all my queries. Thanks.
Ashok
When it came to selecting the right cyber security insurance, SecureNow offered an impressive range of options from reputable insurers.
Pushpa
I appreciated the comprehensive details available for a cyber insurance policy which helped me to make better decisions. Thank you,SecureNow.
Vinay
I recently purchased cybersecurity insurance from SecureNow. The process was straightforward and I felt well-informed throughout, thanks to the clear and concise information provided.
Gaurav
I am delighted with the cyber risk insurance policy I purchased through SecureNow.
Gopal
The entire experience has been nothing short of exceptional. I can confidently say that connecting to SecureNow is one of the best decisions I have made for my cyber liability insurance.
Aman
I bought a cyber security insurance policy from the SecureNow website online for my data in my industry to get protection against any Accidental miss happening. Thanks,SecureNow.
Dinesh
Thanks, SecureNow for offering amazing deals for my cyber risk management insurance.
Vinay
I wanted to buy a cyber extortion insurance but was unable to find the right website. As my colleague suggested, I visited the SecureNow website online which made me purchase pretty good.
Sangeetha
SecureNow has an affordable premium plan, the widest range, in cyber risk insurance policy. It was worth buying.
Prabhu
I recently got to know about cyber insurance and its benefits. So I went on the SecureNow website and researched about it, and finalized the deal.
Sameer
They provide the widest choices of plans and Impressive coverage of cyber security insurance. So I made a purchase there itself. It highly benefits me. Thanks, SecureNow.
Kamlesh
I wanted to buy a cyber insurance policy then someone suggested the SecureNow for their excellence and supportiveness.
Kamal
I contacted SecureNow's team for cybersecurity insurance. They cleared my doubts and I bought the policy. It was a budget-friendly Purchase. Thanks,SecureNow.
Kamaldeep
I got a good deal while purchasing the cyber risk insurance from SecureNow. Thanks, SecureNow.
Vinit
Good Policy, I got protection for my data with cyber liability insurance. Thanks, SecureNow's Team
Kamini
I wanted to buy a cyber security insurance policy. So I visited the website of SecureNow and contacted their team. They provide the best and affordable plans.
Pinku
SecureNow provided me with expert advice for cyber risk management insurance. They are expert in field.
Puneet
It was a good investment. Thanks, SecureNow for helping me find the right cyber extortion insurance.
Reena
I am an old customer of SecureNow. I purchased a cyber risk insurance policy 2 years ago. The coverage has been comprehensive and whenever I had to file a claim, SecureNow responded promptly and took care of all the necessary procedures.
Kamlesh
We always like the comprehensive coverage options for cyber insurance policy provided by SecureNow encompass not only financial losses but also reputational damage, offering a holistic approach to risk management.
Poonam
I always go with SecureNow because of their commitment to ethical practices extends to its claims handling process, prioritizing fairness and transparency in assessing and resolving cyber insurance-related incidents.
Rajini
SecureNow's regular communication about industry trends and emerging threats keeps us informed, allowing us to stay ahead of potential cyber risks in our cyber risk insurance policy.
Vinod
SecureNow's educational webinars and workshops further demonstrate their commitment to empowering businesses with the knowledge to navigate the complexities of cyber insurance.It's very informative for my team.
Vanshika
The adaptability of SecureNow's cyber risk insurance policies accommodates businesses of different sizes, ensuring that each client receives tailored and effective coverage.
Bhavika Kumar
SecureNow's emphasis on building long-term relationships with clients fosters a sense of trust and reliability, making them a preferred choice for my cyber insurance solutions.
Sandeep Ohlan
I must say that SecureNow's commitment to continuous improvement is reflected in its proactive approach to updating and enhancing its cyber insurance offerings.
Abhilash
The educational resources provided by SecureNow with their cyber insurance policy are a valuable addition, helping my businesses stay informed about the latest cyber threats and preventive measures.
Pankaj Mishra
SecureNow's cyber security insurance not only covers financial losses but also includes support for managing the public relations aspect in the aftermath of a cyber incident.
Jignesh
I appreciate SecureNow's dedication to simplifying the often complex language of cyber security insurance policy, making it accessible to a wide range of businesses.
Baljeet
SecureNow's commitment to ethical business practices is evident in the transparency and fairness of its cybersecurity insurance policies.
Sania
The claims process for cyber extortion insurance with SecureNow is efficient and straightforward, providing quick resolution and support during my challenging times.
Parteek
SecureNow's cyber liability insurance plans go beyond traditional coverage, offering innovative solutions for emerging digital risks for our organization.
Anshul Pandey
SecureNow's team goes the extra mile to understand the unique needs of my each business, tailoring cyber risk insurance solutions accordingly.
Parik
The ease of communication with SecureNow's support team makes it easy to get timely assistance for me and also guidance on cyber risk management insurance matters.
Annesha
SecureNow's commitment to customer education is commendable, empowering businesses to make informed decisions about their cyber insurance needs.
Vidya Chauhan
The comprehensive risk assessment with the cyber risk insurance policy provided by SecureNow ensures that our businesses have a clear understanding of their vulnerabilities and can take proactive measures.
Parmeet Verma
As a IT company's head I know about cyber security impotance and believe me that,SecureNow's cyber security insurance policy not only focuses on recovery but also emphasizes preventive measures to minimize the likelihood of cyber incidents.
Parmish Kanojia
We must say that the responsiveness of SecureNow's customer support team instills confidence that assistance is just a call or email away in case of any cyber risk insurance related concerns.
Rahul Kapadia
SecureNow's user-friendly online platform allows for easy policy management, making it convenient for our businesses to stay on top of their cyber insurance needs.
Keshav Kanojia
The commitment to client confidentiality is a strong point for SecureNow, ensuring businesses can trust them with sensitive information related to their cyber liability insurance coverage.
Rajneesh Sukla
SecureNow's dedication to staying abreast of evolving cyber insurance and cyber threats positions it as a reliable partner for our businesses navigating the complexities of the digital landscape.
Babita
The scalability of SecureNow's cyber risk insurance policy plans is particularly beneficial for growing businesses, offering adaptable coverage as their needs change.
Madhav
SecureNow's emphasis on collaboration with clients fosters a sense of partnership, where businesses feel actively involved in shaping their cyber insurance strategy.
Roshan
I got the clarity in communication from SecureNow, both in policy documentation and interactions, contributes to a positive and transparent experience for their cyber security insurance policy clients.
Abdul
SecureNow's commitment to corporate social responsibility is evident in its initiatives to raise awareness about cyber threats and promote digital safety practices.
Naitik
SecureNow's cyber extortion insurance plans are designed with a forward-looking approach, anticipating future threats and ensuring businesses are well-prepared.
Laksh
I admire the flexibility in payment options offered by SecureNow adds convenience for businesses, allowing them to manage their cyber insurance premiums effectively.
Meera Yadav
SecureNow's commitment to fostering a cyber insurance-aware culture is evident in the training resources provided to clients, empowering employees to recognize and respond to potential threats.
Rajat
SecureNow's dedication to innovation is reflected in its use of cutting-edge technology to assess and mitigate cyber risks, providing advanced cyber risk insurance policy for businesses.
Shailesh
I access the securenow's customer service late night but believe me that the accessibility of SecureNow's customer service, available round the clock, is a testament to their commitment to providing timely support for cyber insurance inquiries.
Tushar Bhardwaj
SecureNow's partnerships with leading cybersecurity insurance experts enhance the value of their cyber insurance offerings, ensuring clients benefit from the latest insights and expertise.It's very beneficial for me and my oraganization.
Anshika
The user testimonials and positive feedback about SecureNow's cyber liability insurance further solidify its reputation as a trusted and reliable provider in the industry.
Prashant
SecureNow's commitment to fair and transparent pricing ensures that my businesses receive the best value for their investment in cyber risk insurance policy.
Radhika
The user-friendly educational materials provided by SecureNow serve as a valuable resource for businesses seeking to enhance their understanding of cyber risk management insurance.
Sunil
SecureNow's cyber risk insurance plans are crafted to cater to businesses across various industries, demonstrating their versatility in addressing diverse cybersecurity challenges.
Mohan Khanna
SecureNow's commitment to data protection is exemplified in the robust security measures in place to safeguard sensitive information related to cybersecurity insurance policies. I totally believe in their commitment.
Sheshank
My reason to choose SecureNow is the simplicity of the claims process of cyber security insurance policy with SecureNow minimizes the stress for businesses facing the aftermath of a cyber incident, facilitating a quick and efficient resolution.
Kailash
SecureNow's proactive approach to risk mitigation involves regular updates and recommendations to clients, ensuring their cyber insurance coverage remains effective in the ever-changing landscape.I always like this approach by SecureNow.
Suman Meena
I think they have unbeatable dedication to customer satisfaction is evident in the continuous improvement of their services, based on feedback and evolving cybersecurity insurance trends.
m/s Tech World
In recent past we reporrted a case of cyberbullying in our company. It was unfortunate incedent. We has policy from securenow and insurer provided coverage for losses and further counselling. Glad that we has boughtthe policy.
raghav sharma
We recently bought this extremely crucial Cyber Security insurance to protect our financial interests from prevailing cyber threats. It covers the expenses for psychological consultation as well. We are happy with the purchase.
Infoline Securities
I run a manufacturing company and I recently purchased Cyber Insurance Policy from Securenow, to protect the customers data stored online. Not only that, the policy also provided coverage for legal cost in case any customer sues the company for any reason.
Chandan aneja
We needed Cybersecurity Insurance. In Securenow portal, calculating premiums was so easy and were really impressed by their expert advise. We bought it online, with least efforts.
Xena Desouza
Hello, we bought third party liability under our cyber risk insurance. It also protects us against any claim by the government. It is really good policy. we bought this on Securenow.
Data World Intl
We beleive that third party cyber liability insurance is a must in today's digital era. It can really save you from huge losses during unforseen circumstanve that crop up suddenlty We had bought ours from our insurance pastner SecureNow.
Bansal Online Trading
I have come to really like SecureNow.in this site. It has amazing deals and affordable premiums. I recently purchased my Cyber Security Insurance policy from their site and it has amazing coverages. Really appreciative of their expertise.
Tirpat Singh
For our company we bought Cyber Risk management insurance from securenow.in. Given the previaling cyber risks these days, we needed it urgently. We bought it through online process which was quick and efficient.
Aseem Nadia
Securenow provided us with Cyber extortion insurance for our organisation. We were vulnebale co. to cyber crime and required it as a necessity. We purchased it through an online method that was quick and easy.
Decode Data Solution
hI, I purchased Cyber Risk insurance policy recently as my company have stored almost all customer data online. I went on to Securenow's official website where i could look for a suitable plan. I ended up buying a plan that provides me enough financial protection. I could not imagine having to pay out of pocket.
Insuropedia
What are the different types of Losses Covered by Cyber Risk Insurance?
What are the Common Exclusions of Cyber Risk insurance?
What does a cyber insurance policy cover?
A cyber insurance policy also known as the cyber liability insurance or cyber risk insurance coverage helps organisations to mitigate risk by offsetting costs involved with recovery after a cyber-related security breach or similar event takes place.
Most sophisticated organisations can deploy the best cybersecurity protocols....
Search Insuropedia - Enter Your Question.
Why SecureNow?
Deep Product Knowledge
We have specialized underwriters and tie-ups with international experts.
Cost-effective Insurance
We work with all insurers to get you the best options- both in terms of price and features.
Quick Turnaround Time
Cover notes are issued within hours of request. This documentation is sufficient for any contractual requirement.
Strong Claims Support
We manage all aspects of your claim - from preparing documentation to follow-up with the insurer.
Value-Added Services
We will advice you on risk management best practices.
Policy Administration System (PAM)
See all your contracts renewal information in one place. Place service requests on PAM.